- Web Desk
- Feb 19, 2026
Cybercrime websites selling hacking tools in Pakistan shut down
-

- Web Desk
- Feb 01, 2025
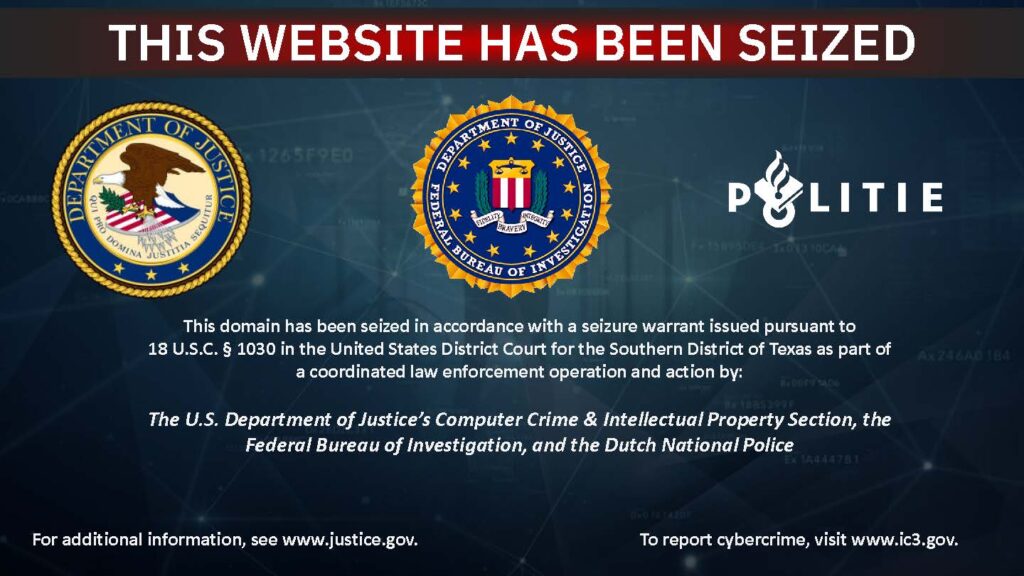
WASHINGTON: A network of 39 cybercrime websites involved in selling fraud and hacking tools has been shut down in Pakistan following an international investigation led by the United States Department of Justice and the FBI.
According to the US Justice Department, the coordinated seizure of 39 domains and their associated servers in an international disruption of a Pakistan-based network of online marketplaces selling hacking and fraud-enabling tools operated by a group known as Saim Raza (also known as HeartSender). The seizures were conducted in coordination with the Dutch National Police.
This group has been active since 2020 and Saim Raza has used these cybercrime websites to sell phishing toolkits and other fraud-enabling tools to transnational organized crime groups, who used them to target numerous victims in the United States, resulting in over $3 million in victim losses.
The Saim Raza-run websites operated as marketplaces that advertised and facilitated the sale of tools such as phishing kits, scam pages, and email extractors, often used to build and maintain fraud operations, according to the US Justice Department.
Sweden releases suspects held in killing of anti-Islam campaigner
Not only did Saim Raza make these tools widely available on the open internet, it also trained end users on how to use the tools against victims by linking to instructional YouTube videos on how to execute schemes using these malicious programs, making them accessible to criminal actors that lacked this technical criminal expertise.
The group also advertised its tools as “fully undetectable” by antispam software.
The transnational organized crime groups and other cybercrime actors who purchased these tools primarily used them to facilitate business email compromise schemes wherein the cybercrime actors tricked victim companies into making payments to a third party, the Justice Department said.
Those payments would instead be redirected to a financial account the perpetrators controlled, resulting in significant losses to victims.
These tools were also used to acquire victim user credentials and utilize those credentials to further these fraudulent schemes.
The seizure of these domains is intended to disrupt the ongoing activity of these groups and stop the proliferation of these tools within the cybercriminal community.
The FBI Houston Field Office is investigating the case.




